As our world becomes more digitized, protecting our communication systems from cyber threats becomes more important than ever. Secure VoIP (Voice over Internet Protocol) is a key player in this fight, keeping business conversations safe from cybercriminals.
Recently, 3CX, a top VoIP solutions provider, has issued a serious warning that sends ripples across the IT sphere: Disable SQL Links now to prevent potential breaches. This isn’t just about fixing a problem—it’s a wake-up call to reassess and strengthen the very foundations of our digital communication infrastructures.
As we explore the details of Secure VoIP and follow 3CX’s advice, let’s approach cybersecurity without complexity. Our goal is crystal clear: to make sure that how we connect and work together remains secure against growing cyber risks.
Let’s go through about the essential steps and strategies to keep your communication channels stable and robust.
What is 3CX?
3CX stands out globally as a top player in IP PBX systems, offering a full suite of VoIP solutions designed for the diverse needs of modern businesses.
Going beyond traditional voice services, 3CX seamlessly integrates video conferencing, live chat, and SMS in a user-friendly package, showcasing its commitment to innovation and transforming how businesses communicate.
The Warning from 3CX

Recently, 3CX has issued an urgent advisory to its users: a critical vulnerability within the SQL link of its system could be exploited if not addressed promptly. This serves as a wake-up call, emphasizing the importance of VoIP security measures and the need for constant vigilance in our digital age.
Notably, 3CX not only identified the risk but also provided guidance on immediate steps to address potential security breaches, showcasing their dedication to user security and trust.
Risks of Unsecured VoIP
Without robust IP PBX security, communication systems become easy targets for cyber threats to communication, including eavesdropping, data theft, and service disruptions. The 3CX SQL link vulnerability serves as a clear example of the dangers lurking in unprotected systems.
Businesses without stringent security protocols expose themselves to a range of cyber threats with potential consequences, from financial loss to irreparable damage to their reputation.
Importance of SQL Links in VoIP
SQL links in VoIP systems, like the backbone of any robust communication network, are responsible for managing data across the unified communications landscape. These links help databases and VoIP systems communicate with each other, allowing for functions like real-time data analysis, managing call details, and giving customers personalized experiences.
But because they’re so important, they’re also a prime target for cyber threats, emphasizing the need for robust data breach prevention measures to uphold the system’s integrity and security.
Steps to Disable SQL Links
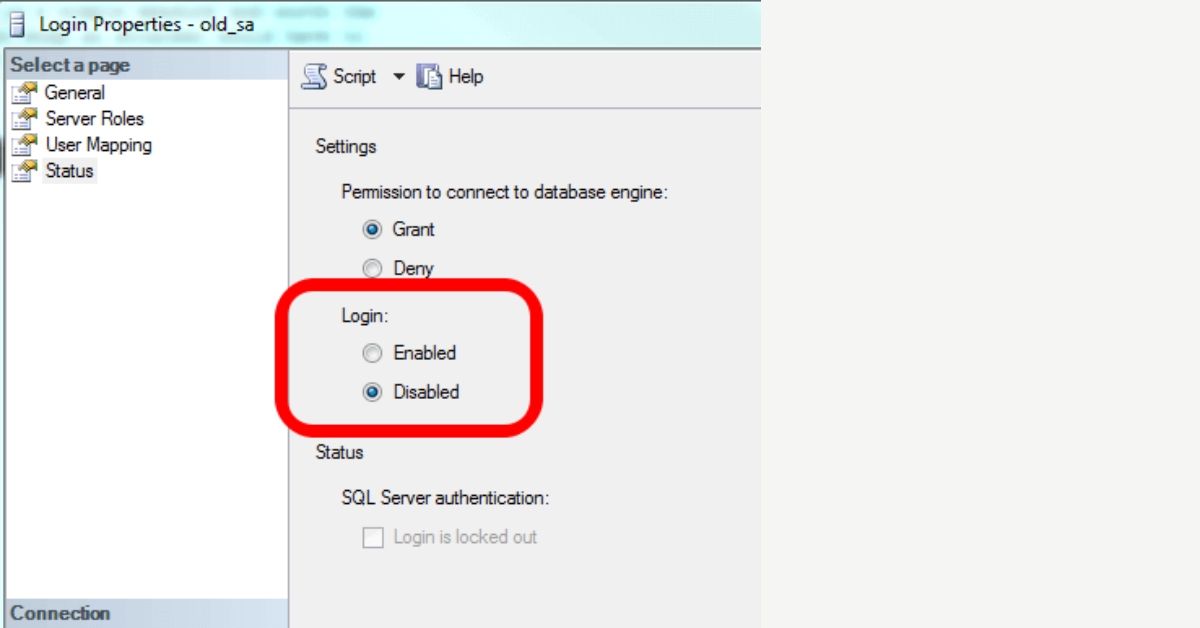
When it comes to safeguarding a VoIP system, turning off SQL links allows you to prevent unauthorized access and avoid potential exploitation. This process involves the following steps –
- Accessing the system’s database configuration
- Identifying specific SQL links
- And executing commands or using network traffic monitoring tools to sever these connections
Following a structured protocol helps avoid unintended disruptions while enhancing the overall security of the VoIP environment.
Best Practices for Secure VoIP
Adhering to unified communications best practices is non-negotiable for securing VoIP against cyber threats. This includes implementing advanced authentication methods for VoIP access, ensuring end-to-end encryption, and regularly updating and patching systems.
Remember to use network traffic monitoring tools to detect anomalies that may indicate a breach. Also, ongoing education on secure VoIP protocols for all users helps maintain a vigilant and informed workforce capable of recognizing and responding to potential security threats.
Importance of Regular Audits

Regular audits are like health check-ups for your organization’s security. They involve thoroughly going through a security audit checklist to ensure every part of your system is fortified against potential breaches.
Audits are all about being proactive and keeping up with the latest in VoIP industry standards and new communication technology to protect your terrain from potential intruders. Audits point out areas for improvement, making sure your defence strategy evolves as your system does.
Ensuring Compliance
Compliance isn’t just about ticking boxes; it’s a commitment to operational excellence and a badge of trust in the industry. It involves aligning your business with industry standards for VoIP and using emerging technologies in communication, such as blockchain for VoIP security, to safeguard communications.
Staying compliant involves keeping up with the latest rules and tech, making security a part of your organization’s core. It’s not just about avoiding fines – it’s about creating a security-focused culture that everyone involved believes in
Bottom Line
The urgent call from 3CX to disable SQL links is more than just a warning – it’s a strong reminder about the importance of digital communication integrity. This proactive approach to cybersecurity is crucial in securing web conferences and maintaining secure VoIP systems.
In the intricate world of online communications, companies like VoIPElements in Melbourne, VIC, lead the way by providing solutions that promise your voice over internet protocol is an asset, not a risk.
Trust VoIPElements to strengthen your communications infrastructure against evolving cyber threats, preserving the confidentiality and continuity of your conversations.


